Across multiple surveys of family office software users, cybersecurity is consistently the single most important and commonly identified item of concern. The potential breach of the family office IT system and the loss of confidential data keep many family office personnel up at night.
And for a good reason. A Boston Private survey titled Surveying the Risk and Threat Landscape to Family Offices found that 26% of family offices have suffered a cyberattack. While traditional security frameworks focus on meeting compliance obligations and preventing unauthorized access to confidential data, cybersecurity in 2022 is more complex—and more comprehensive. Protecting against data breaches and the loss of confidential data is merely one component of a complete and multifaceted cybersecurity framework.
Just as the family office role has evolved over the years, so have its responsibilities. Today, family offices offer clients more than just features and functions. Family offices also must provide the necessary infrastructure, industry certifications, and operations to support the secure and certified operations that their clients demand. Family offices must demonstrate that their clients’ highly confidential data is secure and that their operations support disaster recovery and world-class business continuity.
Family office software companies now must take a more holistic approach to protect family offices from a host of business threats, including cyberattacks, data breaches, and internal and external bad actors—while at the same time dealing with compliance, audits, and governance obligations. Judicious companies recognize they must provide their clients with access to the latest cybersecurity advances while also maintaining greater control over client data—and still offering clients flexibility in their security operations.
The family office’s scope extends beyond its software and data in today’s connected world. Multi-family offices (MFOs) want to offer seamless access and integration (APIs) into their various clients’ internal systems. Their clients want to use these APIs to access governance and use logs to integrate into their corporate compliance and governance tools.
As a result, MFOs want cybersecurity frameworks that are more dynamic and more flexible. Of course, they expect state-of-the-art security of data and systems. But modern MFOs also aim to use these capabilities to differentiate their services and better position their offerings for their clients, highlighting it during the sales cycle to win new deals. In addition, they use their SaaS providers’ infrastructure and offerings to meet their contractual obligations, like pen tests, SOC2 compliance, confidential data access tracking, and more.
Essential family office cybersecurity requirements expected from the family office SaaS provider include the following:
- Flexibility that Accommodates Different Security Needs: The software providers recognize that one security model does not fit all. Some family offices have very sophisticated requirements and need family office software that seamlessly integrates into their identity use compliance and monitoring frameworks. Others require that family office SaaS inherently offers a secure and managed security service, including SOC 2 compliance and security incident management.
- Managed Family Office Cybersecurity Services: Security and compliance are top concerns for organizations moving to the cloud. With a SaaS solution, the SaaS provider handles patching, maintenance, and security vulnerabilities, which relieves the family office of this responsibility and substantially reduces the family office’s operational burden and risk. Imagine not having to worry about whether the family office InfoSec team (which is also generally less experienced than an InfoSec team at a SaaS organization) applied the latest patch to fend off a recent viral software vulnerability or malware that’s bringing down internet services. These managed services include disaster recovery and business continuity support, which mitigates additional risk for the office.
- Inheritable Maturity (Complying with Industry Security Standards and Meeting Statutory and Contractual Obligations): Many family office software customers require compliance with accepted industry standards like SOC 2, ISO 27001, and others. Family offices also must meet national sovereign data residency requirements. In addition, they need to comply with data protection acts like GDPR in the EU, CCPA in California, and the NY DFS. Inheritable maturity allows family offices to inherit their SaaS provider’s infrastructure and security maturity and certifications while leveraging it for their own business goals.
- Client Control over Data: To meet the varying needs of their clients, family offices must join other FinTech companies that allow clients to supply their own encryption key, i.e., Customer Supplied Encryption Key (CSEK). Family offices utilize CSEK to have 100% confidence in data control and assure their clients that only authorized personnel can access their data since they control the encryption keys. In addition, MFOs want the flexibility to segregate the different client data that is managed by various partners using separate unique encryption keys for each client and relationship.
- Transaction-level Access Monitoring that Integrates with Clients’ Governance Tools: SFO/MFO SaaS providers need to provide excellent transactional-level access monitoring. This allows their clients to meet governance obligations of tracking confidential data access. Their clients want to extract these access logs and integrate them with their governance and compliance reports and tools to monitor access. With this dynamism and enhanced capabilities, customers can track and analyze transactions with greater granularity and integrate this metadata and telemetry into additional governance and reporting capabilities. These reports and analytics help improve governance and better understand user behavior.
- Cloud-Native Security that allows Sophisticated Authorization and Access Protocols: A cloud-native Azure Active Directory integration, like in AtlasFive®, enables a team to support very complex requirements from their clients—complexity that isn’t possible with traditional SSO models. For example, a global financial institution may want to separate their SSO authorization model for their users from the authorization model for their client logins. A top-tier security framework will allow this institution to have three separate security domains: one for users to access the family office platform, another active directory for clients (separating them from the internal active directory), and a third for the operations team managing their SaaS system.
An outline of such a family office cybersecurity framework can be seen below. The software, features, and functions are “above the iceberg,” and security is “below the iceberg.”
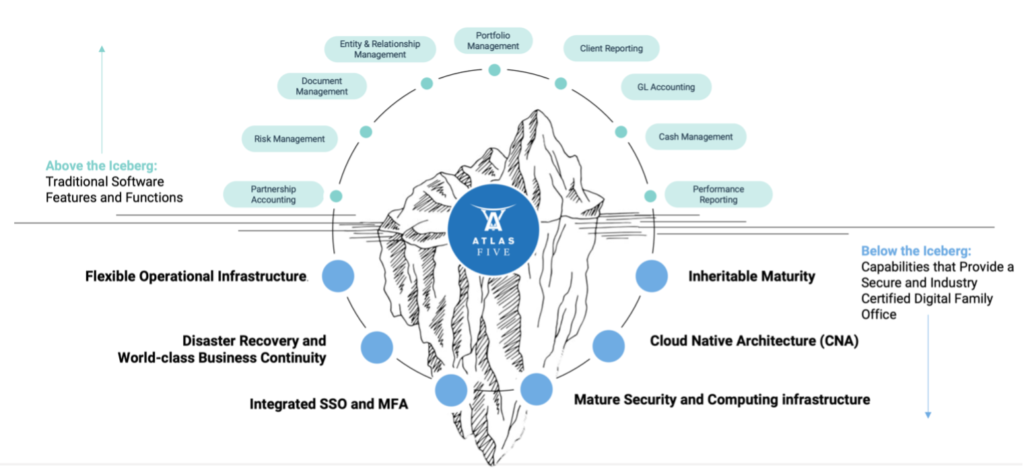
To stay relevant, the modern family office will need to evolve its scope of services—and with those new services come new responsibilities. As the family office performs expanding roles for its clients, it must focus on security to ease growing client concerns over data breaches. Family offices understand this client concern, with 57% of family offices from the Boston Private survey having identified cyber risk as one of the most significant risks they face.
Security—and more specifically, cybersecurity—is shifting from an “afterthought” to a keystone of the family office’s sales pitch. Offices that don’t respond to this transition with a flexible digital platform, like AtlasFIve, and world-class security frameworks will become vulnerable and even obsolete. In this new and ever-changing security environment, family offices need more than a family office application; they need a secure, industry-certified digital family office.




